Quantum computing is predicted to become mainstream within the next 5-10 years. The technology will have a transformative effect on the world, with its ability to solve complex problems much quicker than today’s ‘classical’ computers. However, it also poses a cybersecurity threat that must be taken seriously.
Long-term protection of data is contingent upon the security of the world’s cryptographic infrastructure. This ecosystem survives because it is based on mathematical complexity. The exponential growth in computational power associated with the quantum computer eliminates this safeguard. With quantum computers likely to become viable before a holistic quantum-resistant infrastructure is in place, there is a corridor of uncertainty within which all network transmitted data is vulnerable.
Today’s networks are already vulnerable to a capture now, decrypt later attack, which is why more and more organisations are turning to post-quantum encryption security.

For more information regarding the transition to post-quantum cryptography, speak to one of our consultants today.
What is Quantum Computing?
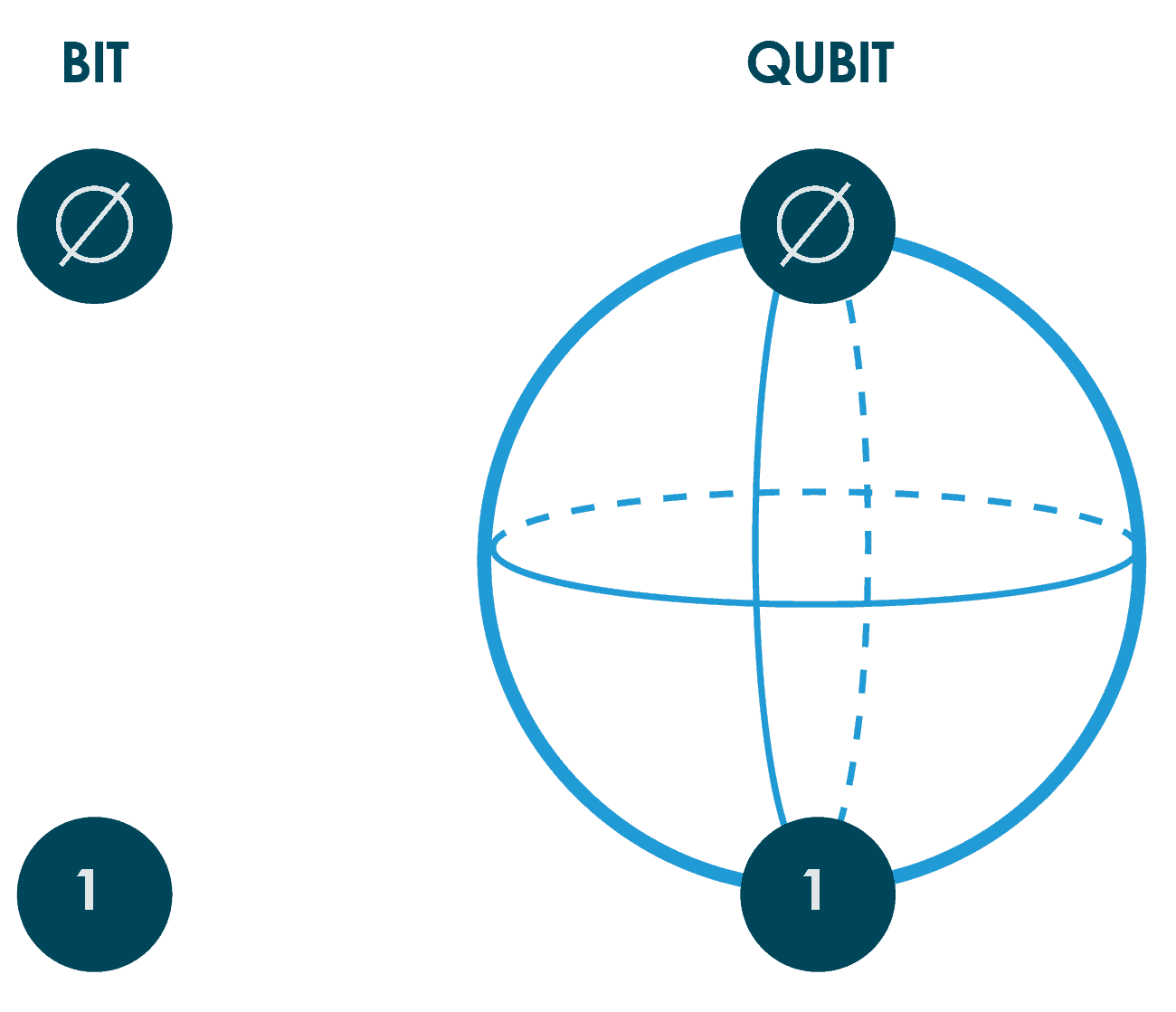
While classical computers code information into bits, sending electrical or optical pulses representing 1s and 0s (a binary code) as first devised by Alan Turing in the 1930s, quantum computers use quantum bits (known as qubits).
These qubits, typically subatomic particles such as electrons or photons, can store information as 1s, 0s or anywhere between these values due to a principle called superposition.
This means that qubits can store more information than bits, and therefore their computational power is exponentially greater.
This will have a transformative effect on areas including scientific and medical research, economic analysis, AI, Big Data, and many other disciplines which require large volumes of data and complex calculations.
How Will Quantum Computing Effect Today’s Cryptography?
Quantum computers will have the ability to do harm. The very same computing power that allows complex problems to be solved can, in turn, be applied to undermine cybersecurity.
Of particular concern is the threat to public key cryptography, which is based on factorisation for RSA algorithms, or discrete log problems with DSA, Diffie-Hellman, and Elliptic-Curve Cryptography (ECC).
While these mathematical problems are sufficient today, a quantum computer running quantum algorithms such as Shor’s or Lov Grover’s could break these codes in a matter of hours, rendering them useless.
To mitigate this risk, organisations must introduce a more quantum resistant stance. This begins with the introduction of post-quantum encryption security.
Quantum Resistant Encryption
While the precise date quantum computing will become mainstream is unknown, it’s generally accepted it will be within the next 5-10 years – well inside many organisations’ IT & cybersecurity systems lifecycle. While the precise date quantum computing will become mainstream is unknown, it’s generally accepted it will be within the next 5-10 years – well inside many organisations’ IT & cybersecurity systems lifecycle. Preparing for this shift requires proactive steps.
Our 5-step guide to Quantum Security provides a practical roadmap to help organisations future-proof their systems and mitigate the risks posed by quantum threats.
Thankfully, quantum-safe cybersecurity technologies that can mitigate the risks of quantum attacks are commercially available today, with further advances due in the near future.
Organisations looking to secure their data in the post-quantum age can begin their preparation with the following steps.
1. Practice Crypto-Agility
A crypto-agile encryption solution allows you to quickly adapt to cryptographic threats by implementing alternative encryption methods.
Senetas encryption solutions leverage state-of-the-art encryption key management and are crypto-agile by design. Importantly, the flexible FPGA design means they can be updated in-field without the need to rip and replace.
Compatible with Quantum Key Distribution (QKD), external sources of entropy such as Quantum Random Number Generation (QRNG) and supporting custom curves and algorithms, Senetas solutions provide long-term data protection in a post-quantum computing world.
2. Undertake a Post-Quantum Risk Assessment
Understand the threats quantum computers will pose to your organization by undertaking a post-quantum risk assessment.
In an ideal world this would mean auditing your entire network, though time and resource may limit this.
Start your audit with business-critical infrastructure as a top priority, before working your way out from there. Remember, a zero trust approach to cybersecurity means securing all of your networks edges, from back-up and DR facilities to branch locations and remote workers.
3. Protect Applications with Quantum Random Number Generation
When generating keys, it is crucial that numbers are seeded from a source that is not vulnerable to bias, or easy to predict. This randomness is already key in today’s cryptography, and will become more so in the quantum era, when quantum computers will be able to ascertain patterns in a fraction of the time it takes their classical counterparts.
Quantum Random Number Generators (QRNGs) provide high entropy and generate a true source of randomness by leveraging principals from quantum physics. Implementing QRNG helps secure vital applications such as cryptographic services, cloud computing and IoT devices.
4. Secure Data in Motion with Quantum Key Distribution
Deploying Quantum Key Distribution (QKD) across mission-critical connected devices ensures forward secrecy and data integrity. QKD uses photons to distribute keys and leverages what’s known as the ‘observer effect’ to verify key authenticity.
If a cyber criminal attempts to intercept this key, the sender and recipient will be alerted, offering them the chance to generate a new key before any sensitive data is transmitted.
5. Implement Quantum Resistant Algorithms
Quantum Resistant Algorithms (QRAs) are algorithms which themselves are designed to remain secure in a post-quantum world. The first generation of NIST shortlisted PQC algorithms for standardization were announced in July 2022, with the final standards expected to be released in 2024.
This doesn’t mean you need to wait until 2024 to start your journey toward quantum resilience. Senetas encryption solutions already feature hybrid encryption: offering the best of todays classical algorithms, plus the NIST shortlisted PQC algorithms.






