Cryptographic Agility
More agile than some might think, the best modern encryption solutions are not only suitable for networks of all shapes and sizes, from modest 10Mbps to ultra-fast 100Gbps speeds, they occupy a barely perceptible presence on the network, are transparent to all other devices and result in minimal latency (frequently less than 4µs at higher speeds).
Bringing Agility to Cryptography
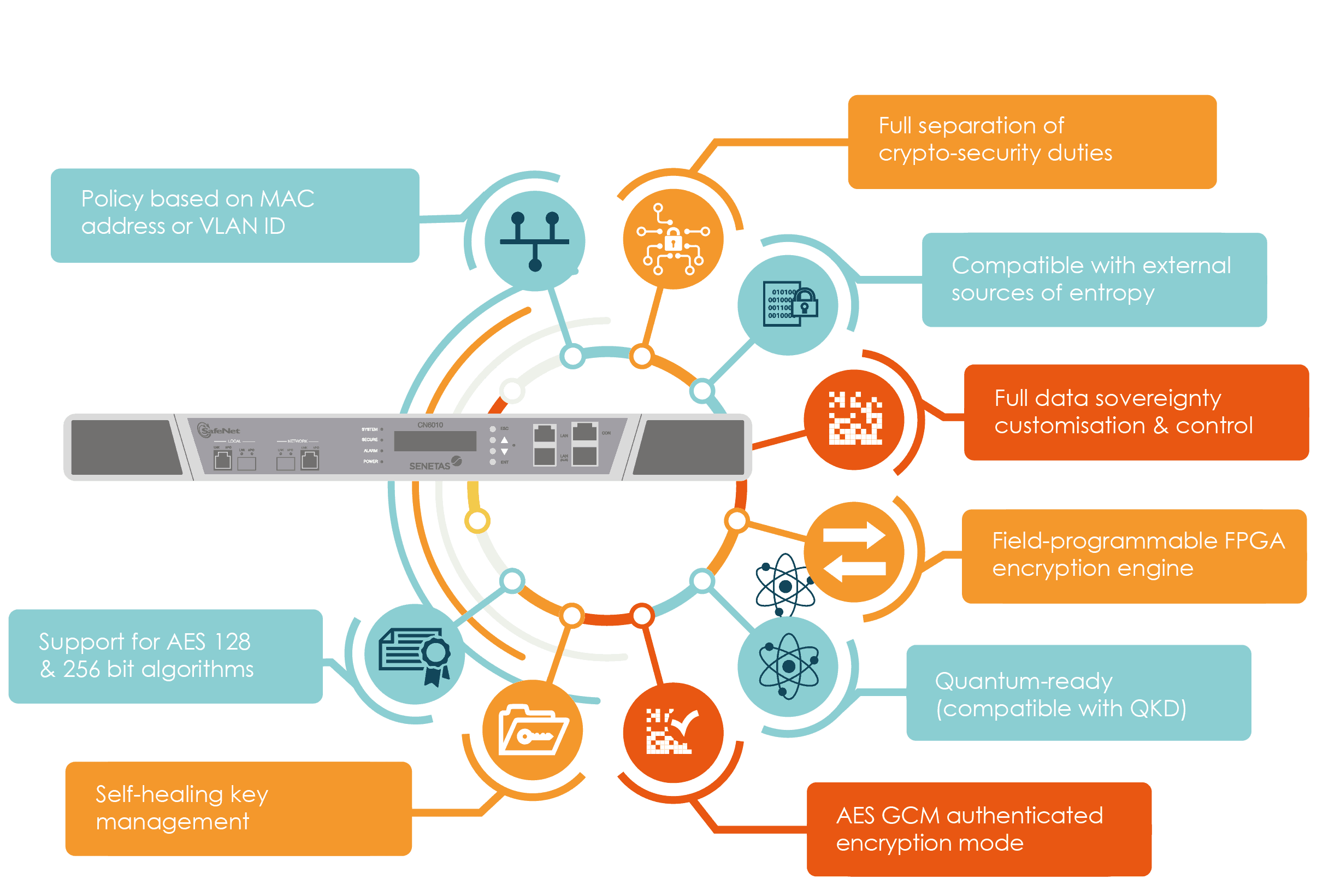
Cryptographic agility, however, is much more than simple performance statistics. It comes from compatibility and interoperability, from FPGA-based flexibility and from the ability to support custom cryptographic agility elements. It even enables a choice of encryption algorithms and standards.
Truly high-assurance encryption solutions are based on standards-based algorithms, typically AES 128 or 256bit. However, If you are able to provide your own, you may prefer to use those; there’s nothing that says you must use the manufacturer’s standard algorithm.
An encryption platform should offer support for as many of these algorithms as possible. For example, CFB (Cipher Feedback) mode, CTR (Counter) mode and GCM – an authenticated encryption mode.
That’s true agility.
Beyond encryption modes, agility should extend to support for other custom components, such as user-defined curves, external certificate authorities and sources of randomness.
Flexible FPGA Architecture
Senetas CN Series hardware encryptors feature advanced FPGA architecture, which enables in-field upgrades (something not possible with embedded encryptors, or lower assurance security devices).
This is a key point of differentiation for Senetas customers, as it effectively future-proofs the technology. If, for example, NIST introduces a new quantum-resistant algorithm in the future; Senetas customers simply load the new algorithm to the system without interruption. This helps to maintain a long-term return on investment and drives down the total cost of owning (TCO) Senetas hardware.
Post-Quantum Cryptography
Since the beginning of the 21st century, technology companies have been investing billions of dollars in the race to develop the first commercially viable quantum computer.
The dawn of the “quantum era” will soon be upon us and promises exponential growth in computing power; leading to significant advancements in the research and development of communications, pharmaceuticals, artificial intelligence and more. However, the quantum computer also poses an existential threat to encryption security as we know it today. It threatens the public key encryption infrastructure that underpins our global digital economy.
Transitioning to post-quantum cryptography
Senetas has been developing solutions to the threat posed by quantum computers for more than 15 years and released its first commercial solution in 2007 in collaboration with IDQuantique. Since December 2021 it has offered hybrid encryption – classical AES and NIST candidate quantum encryption algorithms – in its CypherNET network encryptors. Of the 7 shortlisted candidate algorithms, Senetas already incorporates 4 in its hardware.
The ability to offer both classical and post-quantum algorithms will become the de facto standard for enterprise, government, and defence applications. Truly agile solutions are critical as organisations prepare for the quantum computing era. For detailed guidance on securing data for the quantum age, refer to this comprehensive guide.
Quantum Resistant Algorithms
To mitigate this risk, NIST is working on a program to standardise the next generation of “quantum-resistant” encryption algorithms; designed to remain secure in a post-quantum computing world. The project is well underway, with the first set of candidate algorithms nearing standardisation.
Once standardised the current generation of encryption algorithms will need to be replaced with these new quantum-resistant algorithms. This will ultimately require an update to all software and hardware devices that use Public Key encryption globally. This is not a process that will happen overnight, with most experts predicting a 10 year migration timeline.
With this in mind, Senetas has adopted a strategy to help customers with the transition to post-quantum cryptography. NIST guidelines recommend adopting an embedded classic/quantum state in anticipation of the new standards. Senetas hardware encryptors now support this embedded approach in the form of hybrid encryption – the ability to offer both NIST candidate algorithms and the best of today’s AES standard algorithms. For current customers, hybrid encryption will be available as a free firmware upgrade.
Quantum Key Distribution
Senetas’ end-to-end encryption solutions already feature integrated support for external quantum key generation (QKD), thanks to its long-standing relationship with Swiss Quantum specialists ID Quantique.
The CN Series of hardware encryptors can connect to a QKD appliance via a secure local connection. The QKD appliance connects over a separate fibre optic cable or wavelength to a peer device across the network and exchanges keys using QKD protocols.
Senetas encryptors can then use the QKD keys together with their own keys that are securely distributed across the network using conventional public key techniques. This approach combines the best of classical and quantum key distribution and ensures that, should either approach fail or generate weak keys, there is an additional layer of defence for the customer.
The dawn of the “quantum era” will soon be upon us and promises exponential growth in computing power. However, the quantum computer also poses an existential threat to encryption security as we know it today.








