Network Independent Encryption
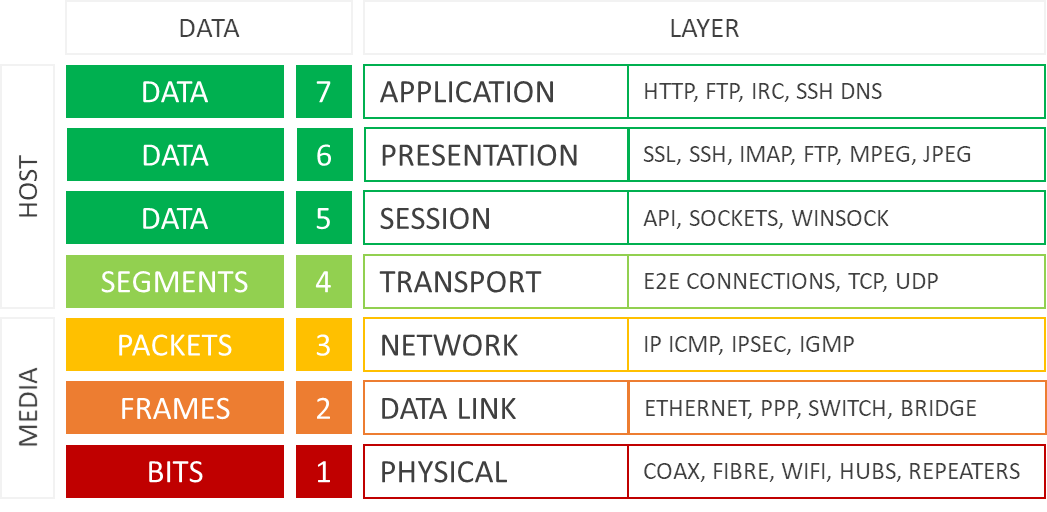
IT and security professionals will be familiar with the Open Systems Interconnection (OSI) model. It’s a visual framework for IT and communications systems that abstracts infrastructure into seven interdependent Layers. One of the foundational models of network infrastructure, it’s been around since the early 1980s.
Senetas hardware has set the standard for secure Layer 2 encryption for many years. However, as networks have evolved to become increasingly virtualised and borderless, there is greater demand to add encryption security at Layers 3 and 4.
The exponential growth in Cloud-enabled services and applications has seen organisations’ data networks become increasingly multi-Layer, particularly in the use of Layers 2, 3 and 4 (Ethernet, Internet Protocol and Transport Layers).
Concurrent, Policy-Based Encryption
With the launch of the CV Series virtualised encryption solution in 2018, Senetas introduced the concept of concurrent, policy-based Network Independent Encryption to meet the evolving needs of today’s multi-Layer networks.
The CV Series enables strong and flexible encryption security across Layers 2, 3 and 4. Centralised management, provided by the Senetas CM7 management application, makes it easy to apply policy settings that meet the varying requirements of multi-Layer networks.
Senetas provides a range of end-to-end encryption solutions that are interoperable and support all topologies; providing organisation-wide data protection.
CN Series hardware provides high-assurance encryption of core IT and network infrastructure data in motion, while CV Series virtualised encryption offers the optimal solution for customers seeking to protect virtualised CPE and WAN infrastructure, all the way to the virtual edge.
Layer 2 Legacy
The demand for Layer 2 networks (Ethernet) grew exponentially in the past 20 years as digitally enabled organisations embraced performance-intensive technologies such as Cloud Computing, UC and Collaboration. As Big Data applications and analytics, and specialist data centres for back-up and disaster recovery, became the business standard, so did high-speed, high-volume data networks.
Layer 2 networks provided the performance necessary for intensive computing tasks, with lower latency and greater flexibility than Layer 3 IP networks. The business case for Layer 2 was strengthened further by transmission efficiency, lower bandwidth costs and economies of scale. They also enable the use of all network architectures, something not possible at Layer 1.
However, when it became necessary for sensitive data to be encrypted, the real benefits of Layer 2 became apparent. When encrypted, Layer 2 networks’ performance was less adversely affected, whereas Layer 3 networks would lose 50% to 70% of their bandwidth and speed performance.
Layer 2 networks became the preferred architecture for mission-critical WAN and MAN operations because they offered reduced complexity, better data latency and reduced management overheads. Layer 2 implementations include:
Cloud Computing – software and infrastructure-as-a-service (SaaS and IaaS)
Data Centre Services – remote storage, back-up and disaster recovery
Big Data Applications – processing, analysis and sharing of information-rich data
SCADA Networks – critical infrastructure and industrial control systems
CCTV and Multi-Media – video, voice and data streaming
Microwave Networks – overcoming physical environment limitations









